Protect Thin Client Deployments With Proven HID Multi-Factor Authentication
Increasingly in our connected world, it is important to know “who” is accessing the IT systems we use to conduct our daily activities. From banks and hospitals to government organizations, retail establishments, educational institutions and other commercial organizations, controlling who can access what network resources is increasingly important to protect these IT systems from malicious take-overs and ransomware due to weak user authentication. From on-premise to remote access to web- and cloud-connected applications, we need high confidence that people are who they claim to be when accessing these critical IT systems.
Virtual Desktops: What They Are and Their Benefits
Virtual Desktop Infrastructure (VDI) is defined as hosting the desktop environment on a central server. It is a form of desktop virtualization where the desktop operating system and applications run within centrally managed virtual machines delivered to the endpoint devices over a network. Those end-point devices can be traditional PCs and laptops repurposed with specialized thin client operating systems, or specialized hardware devices with local operating systems optimized for VDI environment. Virtual desktops allow for new capabilities like shared desktops, which support multiple users, as well as individual desktop virtualization. These systems can be enhanced for improved user security and convenience with single sign-on (SSO) systems and secure remote access, and can be managed by a range of cloud, web and mobile apps to support today’s employee workflows.
From the endpoint perspective, VDI delivers strong cost-savings to deploying organizations by following these key processes:
- The VDI environment is centrally managed. Administrators apply software patches and updates, change configurations and enforce policies for all virtual desktops, reducing the likelihood of security issues vs devices that may not be regularly updated.
- All data resides on the server, not the end client. This offers improved security for data if the endpoint is lost, damaged or stolen.
- Most of the processing for applications in VDI environments is done on high-performance servers. This architecture reduces the need for expensive endpoint hardware, and reduces energy consumption and related building cooling costs.
HID Multi-Factor Authentication: Proven Options for End Users
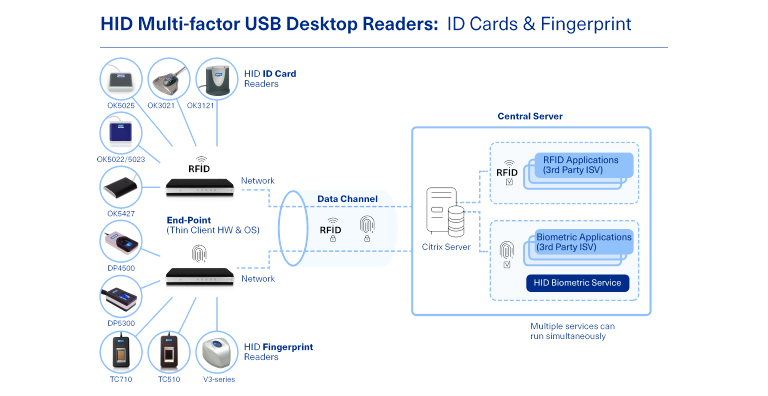
To strongly authenticate end users in VDI environments, HID offers many USB readers that enable multi-factor authentication beyond weak or easy-to-forget passwords. HID partnered with a variety of thin client hardware and operating system providers to ensure these USB readers work efficiently in these IT infrastructures. Our solutions portfolio includes readers like:
- OMNIKEY™ USB card readers that support a range of contact and contactless ID cards, supporting millions of deployed credentials from HID including HID Prox, iClass SE™, Seos™ and HID MobileAccess™, as well as other credentials such as MIFARE™ and DESFire™. OMNIKEY card readers offer proven options to leverage deployed credentials and are available from HID’s global ecosystem of reseller partners.
- HID USB fingerprint readers that provide end users the security and convenience of fingerprint biometrics. These include:
- DigitalPersona™ optical fingerprint readers, widely deployed in logical access applications in banking, enterprise, retail and quick-serve restaurants
- EikonTouch™ capacitive fingerprint readers with on-device matching and encryption, widely deployed in healthcare and government
- Lumidigm™ fingerprint readers provide best in class ability-to-capture and liveness detection and are widely deployed in banking, time/attendance and applications where users may have difficult-to-capture fingers or harsh environments
For information about HID USB readers for ID cards, and fingerprint readers compatible with the growing deployment of virtual desktop infrastructures, visit Single Finger Modules and OMNIKEY Smart Card Readers - Logical Access Control. To learn more about the benefits of VDIs and multi-factor authentication, read our flyer, Virtual Desktop Infrastructure: Proven Endpoint Security Options
Mike leads the product marketing and product management teams, which include biometric and RFID technologies that embed trust into digital devices using innovative authentication technologies. He has over 20 years of product marketing, sales and engineering experience in both the biometric technology and semiconductor industries. Chaudoin holds Bachelors degree in Engineering from Dartmouth College, a Masters degree in Electrical Engineering from the Rochester Institute of Technology and a Masters in Business Administration from MIT's Sloan School of Management.